
From ordering an Uber and booking vacations to work chats and online banking, we rely on our phones for pretty much everything.
But with individuals, companies and even governments falling victim to cyber-attacks, it makes you wonder how safe your personal information actually is.
In a demo shared on YouTube channel Veritasium, hackers infiltrated Linus Tech Tips' phone and exposed some pretty worrying flaws in the phone system.
"We hacked the phone system to spy on [Linus]," the video starts.
Advert
"We intercepted his phone calls and stole his two-factor passcodes. We didn't touch his phone. We didn't send him an email or a text, nothing.
"We did it all remotely and the worst part is it could happen to you."
Here's how they did it.

Signalling System 7 (SS7) is an international telecommunication system that controls how phone calls are routed and billed. It also enables advanced calling features and Short Message Service (SMS).
SS7 was first adapted as an international standard in 1988 and is still in use for both landline and cellphone service today.
But, while it revolutionized the way we communicate, SS7 is incredibly vulnerable to hacking, with some networks selling services to third parties and allowing themselves to be bribed.
Once a hacker has SS7 access, the next step is to collect a phone's IMSI - a unique 15 digit identifier which belongs exclusively to the SIM card of a phone.
Then, it's time to launch the attack.
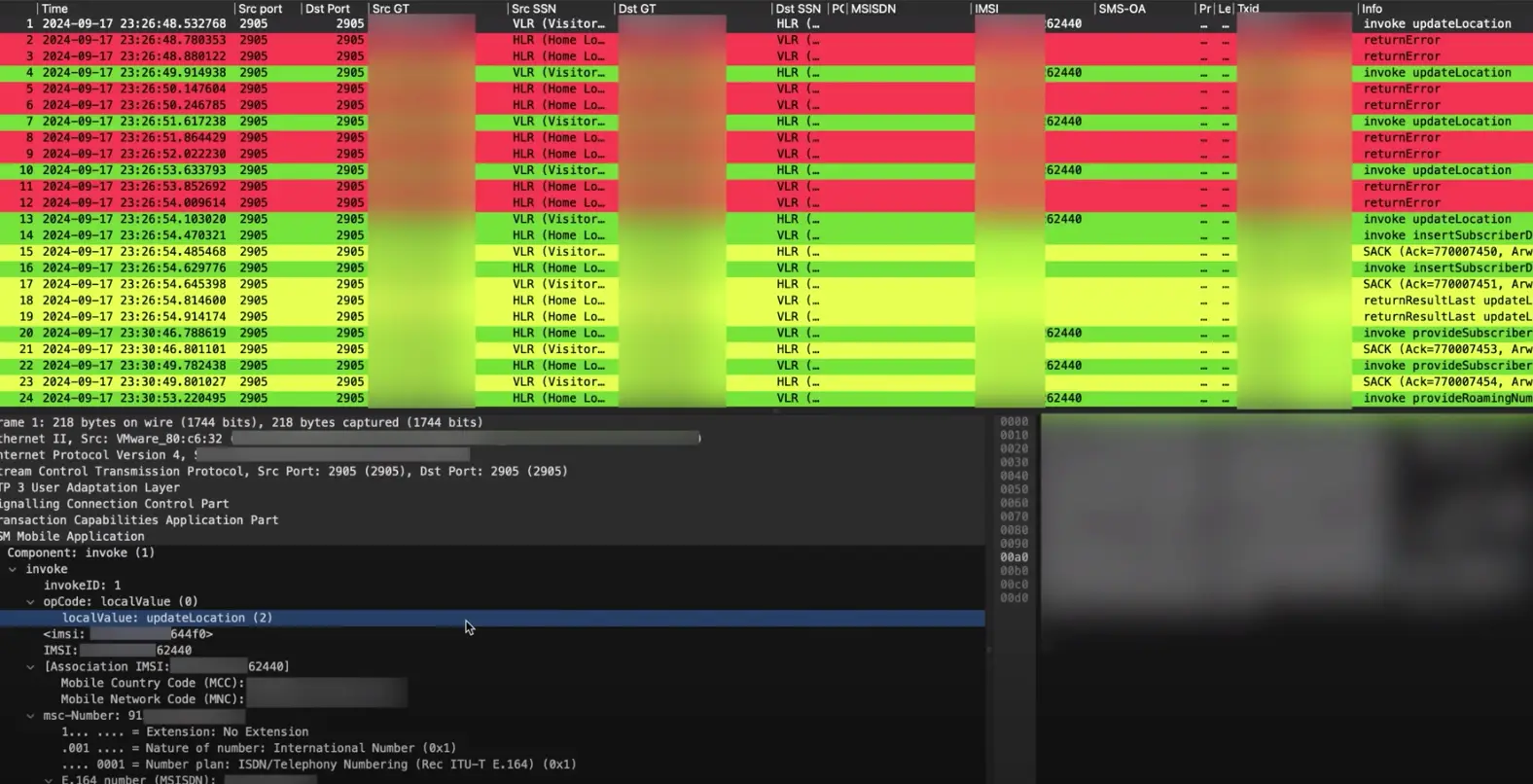
After completing to steps to gain access to Linus' phone (with his knowledge, of course), they ran a test to see if it worked.
A call was made to Linus' phone number, but in a rather eerie moment, he didn't receive it. Instead, Derek (the hacker) intercepted the call and his phone started ringing.
Speaking over video chat, Linus said: "I didn't get it, mine didn't even ring. I heard it ring but I heard it through my speakers on my computer."
Derek then noted: "The crazy thing is that's a regular Canadian SIM card. So any Canadian SIM card, in theory, could be vulnerable to such an attack."
But why were they able to do this?
"When you put a phone number in your address book, you often don't put the country code," an expert explained. "But then if you're in a roaming scenario, that phone number would connect to a completely different person in the country you're currently in.
"By tricking the network into thinking his phone is roaming, we can rewrite the number someone is calling to a number that we control."
As part of the experiment, the team at Veritasium also managed to intercept Linus' text messages and receive a one-time login code sent to his phone.
In further cases they were unable to try out, SS7 can also be used to intercept two-factor passcodes and even track your location.
It's a pretty terrifying thought, but fortunately there are some steps you can take to protect yourself from hacking.
"If possible, choose alternatives to SMS-based two-factor authentication so messages can't be intercepted," Derek advises.
"And, if you're worried about phone tapping, use encrypted Internet-based calling services like Signal or WhatsApp," he says.
